----------------------------------
[UPDATE #01 02/02/2017]: It looks like there's a command line utility to determine what the @GMT path is for previous versions of files/folders called volrest. Worth looking into if you want to find the proper path to use more easily than using vssadmin. Here's another post about it.
----------------------------------
I've seen some chatter about this tweet recently:
Essentially, it's about being able to access and copy files out of Volume Shadow Copies (VSCs) from live systems remotely. There seems to be some confusion related to how this is done. Specifically, I noted a few instances [1] [2] [3] of folks not being able to get it to work. Below, I show how this can and does work. I tested all of this using a Windows 7 VM.
Scenario
You want to copy files directly from a Volume Shadow Copy on a live, remote machine.
The Solution
We have three VSCs: one created on 8/4/2014 07:51:34 PM, one created on 9/19/2016 5:01:19 PM, and one created on 1/31/2017 11:34:16 PM. Let's copy a file from the 9/19/2016 VSC using the proper path syntax -- with specific emphasis on SMB's "previous version token" pathname extension.
Output of commands showing a successful copy operation of one file from a localhost VSC (127.0.0.1).
PS C:\Windows\system32> Test-Path C:\Users\4n6k\readme.txt
False
PS C:\Windows\system32> Copy-Item -Path \\127.0.0.1\C$\@GMT-2016.09.19-23.01.19\Users\4n6k\Desktop\SysinternalsSuite\readme.txt -Destination C:\Users\4n6k
PS C:\Windows\system32> Test-Path C:\Users\4n6k\readme.txt
True
As we can see, the copy succeeded. The Test-Path Cmdlet is initially run in our PowerShell session to show that readme.txt does not exist at the path specified. Once we run our copy operation using the Copy-Item Cmdlet, we can see that this same Test-Path check returns True, indicating that the file now exists.
Note: @GMT Timestamp Format
An important item to note is that the timestamp you use in the path must be the VSC creation timestamp in GMT, and it must be in 24hr military time format (i.e. not AM/PM; not your local time). My machine's system time was set to Central (US). Therefore, I had to apply the correct time offset (+6) to get the VSC creation time of 5:01:19 PM Central converted to 23:01:19 GMT. This time has to be exactly correct to the second, or this whole thing won't work at all. Also, fun fact: the offset might be based on your machine's current time zone or DST status and NOT the time zone of when the VSC was created. Note that one of the VSCs' creation times is in September and one is in January. In the Central (US) time zone, September falls within Daylight Savings Time while January does not. Despite this time difference, to copy out the files from each one of these VSCs, I had to apply an offset of +6 to get the correct path and for the copy to succeed. To further prove this point, take a look at what time is displayed when I browse the September VSC with Windows Explorer:
Before pressing Enter:
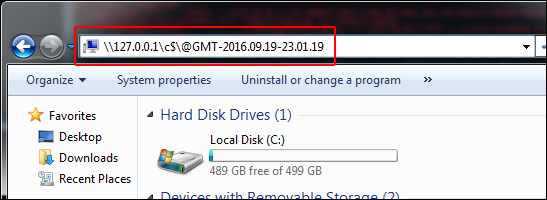
After pressing Enter:
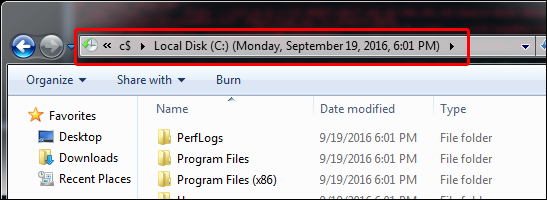
An important item to note is that the timestamp you use in the path must be the VSC creation timestamp in GMT, and it must be in 24hr military time format (i.e. not AM/PM; not your local time). My machine's system time was set to Central (US). Therefore, I had to apply the correct time offset (+6) to get the VSC creation time of 5:01:19 PM Central converted to 23:01:19 GMT. This time has to be exactly correct to the second, or this whole thing won't work at all. Also, fun fact: the offset might be based on your machine's current time zone or DST status and NOT the time zone of when the VSC was created. Note that one of the VSCs' creation times is in September and one is in January. In the Central (US) time zone, September falls within Daylight Savings Time while January does not. Despite this time difference, to copy out the files from each one of these VSCs, I had to apply an offset of +6 to get the correct path and for the copy to succeed. To further prove this point, take a look at what time is displayed when I browse the September VSC with Windows Explorer:
Before pressing Enter:

After pressing Enter:

But let's not stop there. Instead of copying just one file, let's copy a whole directory from the VSC.
Output of commands showing a successful copy operation of a directory from a localhost VSC (127.0.0.1).
This copy also succeeded. We can see the contents of the copied SysInternals directory in the destination folder via Get-ChildItem's recursive output.This is all fine and good, but up to this point, we've just been copying items from our local machine's VSCs. Now that we know that the above process works locally, we should be able to apply it to remote machines fairly easily. So let's do that.
There are many ways to copy/exfiltrate data off of remote machines, but...let's keep it simple. From a separate machine, let's connect to the [now] remote host that contains the VSCs in question using admin creds. Let's also copy readme.txt:
Output of commands showing successful connection to remote host and copy operation of one file from Sept VSC (192.168.1.199).
C:\Windows\system32>net use \\192.168.1.199\C$ /user:4n6k
Enter the password for '4n6k' to connect to '192.168.1.199':
The command completed successfully.
C:\Windows\system32>IF EXIST C:\Temp\Exfil\readme.txt ECHO FILE EXISTS
C:\Windows\system32>copy \\192.168.1.199\C$\@GMT-2016.09.19-23.01.19\Users\4n6k\Desktop\SysinternalsSuite\readme.txt C:\Temp\Exfil
1 file(s) copied.
C:\Windows\system32>IF EXIST C:\Temp\Exfil\readme.txt ECHO FILE EXISTS
FILE EXISTS
As we can see, a simple connection is made to the remote host using net use (w/ elevated creds), and the readme.txt file from the remote host's September 2016 VSC is copied using the SMB "previous version token" pathname extension.
[UPDATE #01 02/02/2017]: If we want to make the @GMT path lookups even easier, we can run a command line tool called volrest. We don't even have to run it as admin:
Output of unelevated volrest.exe showing @GMT VSC path names on localhost C$ for a specified location, recursively..
It should be noted that you will get more results by running volrest as admin, but you will still be able to identify the @GMT paths and get a good amount as a standard user. There are some key files/directories that will not be shown if you run as a standard user; here's a sampling of some files/folders I couldn't see when specifically querying system32:
Sample of files/folders that were not returned when running volrest.exe across system32 as a standard user.
The command run was .\volrest.exe \\127.0.0.1\C$\Windows\system32 /s. Running as a standard user returned 257 files + 26 dirs; running as admin returned 323 files At the end of the day, this technique does work. Can it be used to more easily pull VSC contents for use in forensic investigations? Sure. Could it also be used to exfiltrate data that may otherwise not look to be immediately available on a given machine? Oh yes.
This is a double-edged sword if I've ever seen one.
-4n6k
References
1. SMB @GMT Token
2. SMB Pathname Extensions
3. Reference to Original Tweet 01
4. Reference to Original Tweet 02
5. Reference to Original Tweet 03 - Tools (by Harlan Carvey)









5 comments:
Dan,
You seem to have gotten the copy command to work for remote systems, but not for the local system. Is there a reason you chose to use PowerShell over the 'copy' command?
@Harlan: No reason in particular. It was more of a way to show the different approaches for doing this; it should work either way.
I still can't get this to work on a local system (have not tried remote). Not sure why it doesn't work for me on Windows 7/8/10.
Oh my goodness. I my looking for the same post for fixing some https://www.huffpost.com/archive/ca/entry/to-pay-or-not-to-pay-someone-to-write-my-essay-for-me_b_14793970 login problem. It's great to find the solution on your page. Keep sharing informative content for the readers.
This is happening on my new home computer using the exact jargon and well as a bridege \\localhost\C$\@GMT-2025.05.11-18.36.17\hp\bridge How do I remove, I am a non-IT part of a domestic violence organization.
Post a Comment